Here is the spam millions of netizens found in their mailboxes:
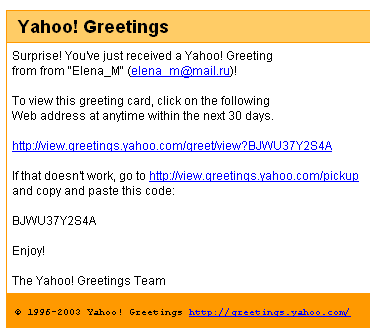
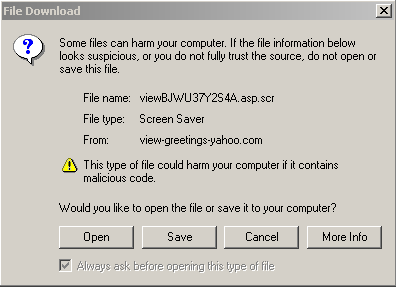
Attempts to view the card did lead (depending on your browser security configuration) to the following offer for a screensaver from the http://view-greetings-yahoo.com site:
Basic Analysis
Obviously somethings is fishy here: well behaved greeting cards do not aspire to camp on one’s hard drive. The attentive reader will also have noticed that the effective url, view-greetings-yahoo.com differs markedly from the initial view.greetings.yahoo.com… but how many average netizens pay attention to those details? Besides, even if they bother to check the web server at view-greetings-yahoo.com they risk being deceived as it looks exactly as the main Yahoo! server at view.greetings.yahoo.com.
We decided to investigate this “greeting card” further and downloaded the alleged screen saver. Once run, it simply displays the following message:
Error on line 25: invalid object
An average user would dismiss the message and forget about it. Behind the scene however, another program called sysman32.exe has been downloaded and is ready to run at the next reboot. Sysman32.exe aims where it hurts: at the user’s wallet. Active in memory, it monitors the web browser windows and attempts to steal the credentials the user uses to access his webmoney wallet, his paypal account, his “Gold” accounts (whatever that means) or, in a generic way, the passwords the user uses to access the pages where he “signs-in”. When its fishing expedition pays off, the trojan e-mails its bounty home.
More specifically, the trojan:
- creates a hidden window and a couple of timers
to monitor web browser connection windows.
-
Then,
- Once every 2 minutes it checks if the foreground window has “WebMoney Keeper” title. If that is the case, it sends the collected information to the mail server.
- Once every
minute it checks if any web browser window has an interesting title
- e-gold Account Access
- PayPal – Log In
- – Sign In
and if such a window is found, it collects all the information from its input fields.
- Patches your webmoney program (wmclient.exe) to get information from you digital wallet.
-
Steals the contents
of the SOFTWARE\Webmoney\Options registry key and stores it
in the following files:
- c:\~fe0273.tmp
- c:\6783f.tmp
- c:\3f45e.tmp
- \xfm1.txt
-
Sends the collected
information to the mail server at this IP address
62.84.131.172.
The recipient names are
zkeeper@centrum.cz, kadabra@centrum.cz,
and unclebill@centrum.cz, the from field is
support@microsoft.com.
-
Then,
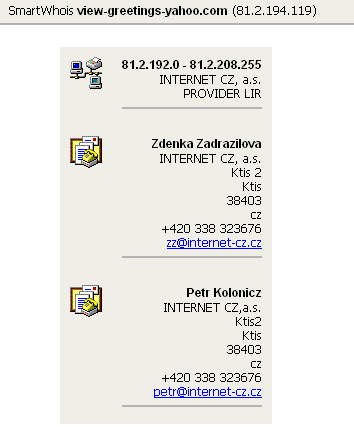
As mentioned above, while the web page (and the mail server) is registered in the Czech Republic, all its components are the actual Yahoo components as all requests are redirected on the fly to the normal Yahoo server. A casual check will not reveal the deception.
Note : today (march 19, 2003), the mail server refuses all connections because it seems overloaded and the web page seems to be down. (Is the scam successful or are white hats overloading it?)

